PakAlumni Worldwide: The Global Social Network
The Global Social Network
Proliferation of Cyber Hacking Tools in Pakistan
Many intelligence agencies are turning to the use of smartphone malware and spyware for the purpose of hacking and surveillance. The list of such agencies includes but not limited to US CIA, NSA, Mossad, RAW, MI6, ISI and others. Global proliferation of cyber hacking tools appears to have been accelerated with the US CIA's loss of control of its hacking tools including spyware, malware, viruses and trojans.
Stealth Mango and Tangelo:
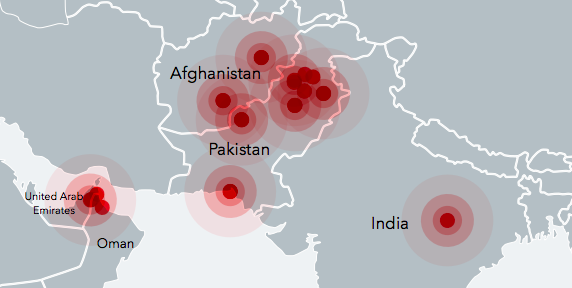
Lookout, an American mobile security firm based in San Francisco, has recently published a report claiming that a "group or individuals that are believed to belong to the Pakistani military "has developed and released a "set of custom Android and iOS surveillanceware tools we’re respectively calling Stealth Mango and Tangelo". The report says: "These tools have been part of a highly targeted intelligence gathering campaign we believe is operated by members of the Pakistani military". The countries affected by it include Afghanistan, India, Iraq, Pakistan and the United Arab Emirates, according to Lookout report.
The targets in Pakistan include members of the foreign diplomatic corps who have visited conflict zones, particularly parts of Balochistan, and Pakistani officials involved in internal corruption investigations.
The goal of the Lookout report is to sell their security software as obvious from their concluding summary below:
"Stealth Mango and Tangelo is yet another example among the numerous campaigns we have uncovered (Dark Caracal, ViperRAT, FrozenCell, etc.) where threat actors are developing in-house custom surveillanceware. The actor behind Stealth Mango has stolen a significant amount of sensitive data from compromised devices without the need to resort to exploits of any kind. The actors that are developing this surveillanceware are also setting up their own command and control infrastructure and in some cases encountering some operational security missteps, enabling researchers to discover who the targets are and details about the actors operating it that otherwise are not as easily obtained. Relevant data has already been shared with the appropriate authorities. Lookout customers are protected against Stealth Mango and Tangelo and have been for several months since the beginning of the investigation."
Amnesty International Allegations:
Amnesty International has alleged that attackers are using fake online identities and social media profiles to "ensnare Pakistani human rights defenders online and mark them out for surveillance and cybercrime". The report titled "Human Rights Under Surveillance: Digital Threats against Human Righ..." claims that Diep Saeeda, a Lahore-based human rights activist, has been targeted by a "network of individuals and companies based in Pakistan that are behind the creation of some of the tools seen in surveillance operations used to target individuals in Pakistan".
Amnesty says that "over the course of several months, Amnesty International used digital forensic techniques and malware analysis to identify the infrastructure and web pages connected to online attacks on human rights activists in Pakistan". "Amnesty International’s Technology and Human Rights team has been able to trace these attacks to a group of individuals based in Pakistan".
Proliferation of Hacking Tools:
In 2017, Wikileaks revealed that the American intelligence agency CIA has "lost control of the majority of its hacking arsenal including malware, viruses, trojans, weaponized "zero day" exploits, malware remote control systems and associated documentation." The Wikileaks noted that that "the CIA made these systems unclassified".
Wikileaks said: "In what is surely one of the most astounding intelligence own goals in living memory, the CIA structured its classification regime such that for the most market valuable part of "Vault 7" — the CIA's weaponized malware (implants + zero days), Listening Posts (LP), and Command and Control (C2) systems — the agency has little legal recourse".
FBI agents have since arrested 29-year-old former CIA software engineer Joshua A. Schulte as a prime suspect in the release of the CIA documents via Wikileaks, according to New York Times.
It appears that the CIA's "hacking arsenal" is now being modified and used by many state and non-state actors to carry out hacking and surveillance of their targets around the world. The proliferation of cyber hacking tools appears to be a lot easier than the proliferation of the nuclear weapons technology.
Summary:
A report by American mobile security software vendor Lookout claims that individuals and groups connected to the Pakistani military are using spyware and malware tools on targets in Afghanistan, Pakistan, India and UAE. Amnesty International alleges that Pakistan intelligence agencies are "network of individuals and companies based in Pakistan that are behind the creation of some of the tools seen in surveillance operations used to target individuals in Pakistan".
Many intelligence agencies are turning to the use of smartphone malware and spyware for the purpose of hacking and surveillance. The list of such agencies includes but not limited to US CIA, NSA, Mossad, RAW, MI6, ISI and others. Global proliferation of cyber hacking tools appears to have been accelerated when the US CIA lost control of its hacking tools including malware, viruses and trojans.
Related Links:
Pakistan Operation Arachnophobia
Revolution in Military Affairs: Cyberweapons and Robots
Pakistani-American Founder of Fireeye Cyber Firm
Pakistan Boosts Surveillance to Fight Terror
Pakistan's Biometric Registration Database
Ex Indian Spy Documents RAW's Successes in Pakistan
Intelligence Failures in Preventing Daily Carnage in Pakistan
What If Musharraf Had Said NO to US After 911?
Pakistani Computer Scientist Fights Terror
-
Comment by Riaz Haq on May 23, 2018 at 8:29pm
-
Pakistan’s first-ever Cyber Security Centre launched
Aims to develop tools and technologies to protect cyberspace, sensitive data and local economy from the cyber-attacks
https://gulfnews.com/news/asia/pakistan/pakistan-s-first-ever-cyber...
Pakistan government’s Cyber Security Centre has been inaugurated at Air University in Islamabad to deal with cyber security challenges in the digital age.
-------------
Faaiz Amir informed that Air University is also commencing a four year BS cyber security programme, which is designed to develop modern cyber security skills and apply them to manage computers, systems, and networks from cyber-attacks. The programme would increase the awareness and knowledge about cyber security in Pakistani students, he added.
------------
Cyber security encompasses technologies, processes and controls that are designed to protect systems, networks and data from cyber attacks. Pakistan’s Cyber Security Centre aims to develop advanced tools and research technologies to protect Pakistan’s cyberspace, sensitive data, and local economy from the cyber-attacks.
The headquarter of the National Centre for Cyber Security will be based at Air University Islamabad with labs at different universities of Pakistan including Bahria University Islamabad, National University of Science and Technology (NUST), Information Technology University Lahore (ITU), Lahore University of Managment Sciences (LUMS), University of Peshawar, University of Engineering and Technology Peshawar, University of Nowshera, Pakistan Institute of Engineering and Applied Sciences (PIEAS), NED University Karachi, University of Engineering and Technology Lahore and University of Engineering and Technology Taxila.
Cyber-attackspose an enormous threat to the national economy, defence and security, National Security Adviser, Nasser Khan Janjua, earlier said.
After repeated calls from experts to secure the cyber space, Pakistan government has finally launched the centre to protect the cyberspace, sensitive data, and local economy from the cyber-attacks.
Last week, country’s National Counter Terrorism Authority (NACTA) also established a cyber security wing on modern lines to evolve cyber security strategies and to meet emerging cyber terrorism threats.
-
Comment by Riaz Haq on May 25, 2018 at 8:13am
-
https://gpinvestigations.pri.org/how-north-korean-hackers-became-th...
How North Korean hackers became the world’s greatest bank robbers
Patrick Winn May 16
Asia correspondent for PRI and GlobalPost Investigations• RFK Award Winner • Author of HELLO, SHADOWLANDS, available on
The Reconnaissance General Bureau, North Korea’s equivalent to the CIA, has trained up the world’s greatest bank-robbing crews. In just the past few years, RGB hackers have struck more than 100 banks and cryptocurrency exchanges around the world, pilfering more than $650 million. That we know of.
It was among the greatest heists against a United States bank in history and the thieves never even set foot on American soil.
Nor did they target some ordinary bank. They struck an account managed by the Federal Reserve Bank of New York, an institution renowned for its security.
In vaults 80 feet below the streets of Manhattan, the bank holds the world’s largest repository of gold. Many of these gold bars belong to foreign governments, which feel safer storing their gold inside well-defended bunkers in America than at home.
By the same token, overseas governments also store cash with the Fed. But this is cash in the 21st-century sense: all ones and zeroes, not smudgy bills. The bank holds vast foreign wealth on humming servers wired up to the internet.
That’s what the thieves went after in February 2016: nearly $1 billion, sitting in a Fed-run account. This particular account happened to belong to Bangladesh. Having already hacked into the servers of the Bangladesh Central Bank, the criminals waited until a Friday — a day off in many Muslim-majority nations, Bangladesh included.
Then they started draining the account.
Posing as Bangladesh Central Bank staff, the hackers sent a flurry of phony transfer requests to the Fed totaling nearly $1 billion. The Fed started zapping cash into accounts managed by the thieves overseas, most of them in the Philippines. Much of the money was quickly pulled out as cash or laundered through casinos.
From there, the trail goes cold.
The hackers didn’t get the full billion they desired. Most of the bogus requests were caught and canceled by suspicious personnel. But they did end up with an amazing score: $81 million.
The culprits of this heist are loyal to one of the most impressive organized crime syndicates in the world. They don’t work for the Triads, nor the Sinaloa Cartel, nor Sicily’s Cosa Nostra. They are agents of the Reconnaissance General Bureau (or RGB), which is headquartered in Pyongyang. This is North Korea’s equivalent to the CIA.
Like the CIA, North Korea’s RGB is steeped in clandestine overseas plots: assassinations, abductions and lots of spying. But it is perhaps better understood as a mash-up between the CIA, the KGB and the Yakuza.
What distinguishes the bureau is its entrepreneurial streak — one with a distinctly criminal bent.
For decades, North Korea has been beleaguered by Western sanctions and barred from global markets. This has prodded the regime to seek revenue in darker realms that are beyond the law. These black-market enterprises have included heroin production, printing bogus $100 bills and counterfeiting name-brand cigarettes.
But all of those rackets have now been totally eclipsed by hacking. The bureau has trained up the world’s greatest bank-robbing crews, a constellation of hacking units that pull massive online heists.
These thieves also have one distinct advantage over other syndicates: They are absolutely confident that they’ll never be charged. So it goes when your own country sponsors your criminal mischief.
This is a new phenomenon, according to US intelligence officials. “A nation state robbing banks … that’s a big deal. This is different,” says Richard Ledgett. He was, until his recent retirement, the deputy director of the National Security Agency.
-
Comment by Riaz Haq on May 26, 2018 at 10:20am
-
Afghan diplomats in Pakistan targeted by 'state-backed hackers'
By Secunder Kermani
BBC News, Islamabad
http://www.bbc.com/news/world-asia-44250769
Afghan diplomats in Pakistan have been warned they are believed to be victims of "government-backed" digital attacks trying to steal their email passwords.
Afghan embassy sources told the BBC two staff members and a generic account received alerts from Google this month.
Last week Amnesty International detailed attempts to install malware on computers and phones of activists critical of Pakistan's military.
The army did not comment on allegations intelligence services were to blame.
After the Google warning alerts were sent out, another Afghan diplomat's email account was hacked and made to send out emails, without his knowledge, containing suspicious attachments.
The emails purported to contain photographs of rallies by protesters known as the Pashtun Protection Movement (PTM). In fact the attachments appear to contain malicious files, although it was not possible to download and examine them.
The PTM movement has accused the Pakistani military of committing human rights abuses in the country's fight against terrorism. Protests have been non-violent but controversial due to their unusually direct criticism of the Pakistani intelligence services.
Why were the emails sent?
Supporters of the Pakistani military have accused the PTM of working on behalf of the Afghan intelligence services - the two countries regularly accuse each other of working to undermine the other's security.
A source in the Afghan embassy told the BBC he was concerned that recipients of the emails sent out from the diplomat's account could believe the Afghan embassy was linked to the movement.
The email was sent to addresses publicly linked to a number of political figures in Pakistan. They include a former information minister, and a former law minister.
It was also sent to a former senator from a Pashtun nationalist party, Bushra Gohar. Ms Gohar told the BBC: "I know for a fact that all my accounts are being observed… this is condemnable."
She added: "Parliament needs to form a committee and look into what is going on."
Have there been other cyber-attacks?
An employee of the Afghan embassy and a former member of staff were also both targeted by a fake Facebook profile linked to cyber-attacks.
A report by Amnesty International released last week revealed that the profile, "Sana Halimi", had repeatedly sent malware to a human rights activist in Lahore.
One of the Afghan embassy staff members befriended by "Sana Halimi" told colleagues "she" had engaged him in conversation pretending to be an Afghan woman from the city of Herat.The Facebook account also befriended a number of other human rights activists. One told the BBC it had messaged him in a "flirtatious" manner.
In a report released last week, mobile security company Lookout documented "Sana Halimi" sending out malware via Facebook Messenger on at least two occasions.
The incidents form part of an investigation they carried out into the successful hacking of devices by a team they describe as "likely" being run by the Pakistani military. Their report examined around 30GB of stolen data, a significant part of which appeared to have been taken from Afghan officials.
Who was 'Sana Halimi'?
The BBC has learnt that the pictures of "Sana Halimi" were in fact stolen from the social media accounts of a 21-year-old chef in Lahore called Salwa Gardezi with no connection to Afghanistan.
Ms Gardezi is a close relative of a prominent political commentator, Ayesha Siddiqa, known for her work critiquing the Pakistani military. It is not clear if her photographs were used because of this connection.
Ms Gardezi said she had only realised her pictures had been copied from her Facebook and Instagram accounts after a BBC article on the malware attacks last week. She told the BBC it was "shocking" her images had been used in this way, and that she had "no connection" to political work at all.
She added that she is planning to lodge a complaint with Pakistan's Federal Investigations Agency as she is concerned she could wrongly be mistaken as being linked to the cyber attackers.
"I want to clear my image," she said.
-
Comment by Riaz Haq on December 4, 2018 at 10:21pm
-
#Turkey's STM will organize training in #cybersecurity and #infornation #tech at #Pakistan Air #University; organize international conferences; give consultancy to research projects and support infrastructure for National Cyber Security Center at Air Uni. https://www.armyrecognition.com/ideas_2018_news_official_show_daily...
At IDEAS 2018, a Document of Understanding (DoU) was signed by STM and Pakistan Air University under the leadership of the Presidency of Defence Industries (SSB) of the Presidency of Rebuplic of Turkey. With this agreement, STM will provide significant solutions in integrated cyber security, big data and IT domains.
STM SavunmaTeknolojileriMühendislikveTicaret A.Ş. expands its business in Pakistan. Following the cooperation in naval programs under the leadership of the Presidency of Defence Industries, it now moves to different areas.
The signing ceremony was held with the participation of Mustafa Murat Şeker, SSB Vice President; Murat İkinci, STM General Manager; Air Vice Marshal Faaiz Amir, Vice Chancellor of Pakistan Air University; and officials. The agreement will increase the cyber security capabilities of Pakistan Air University, which sets up cyber security strategies of Pakistan and is responsible for the establishment of Pakistan’s National Center of Cyber Security (NCCS).
STM will organize special training and internship programs in cyber security and IT for Pakistan Air University students and faculty; organize international conferences and workshops; give consultancy to research projects in graduate programs; and support the infrastructure for the establishment of the National Cyber Security Center (NCCS) at the university. This agreement aims to increase the national cyber security capabilities of the friendly country Pakistan thanks to STM's integrated cyber security efforts and capabilities.
-
Comment by Riaz Haq on December 4, 2018 at 10:33pm
-
#Israeli #Cybersecurity Firm NSO Accused Of Helping #Saudis Spy On #Khashoggi. #Israel is actually involved in NSO in that Israeli government officials have to give the OK to let it sell its products abroad. This company has faced a lot of controversy. https://n.pr/2ANSZea
DANIEL ESTRIN, BYLINE: Hi.
MARTIN: Tell us more about these allegations, and what do we know about the Saudi dissident making them?
ESTRIN: His name is Omar Abdulaziz. He tells a very compelling story. He's a social media activist. He's a critic of the Saudi royal family. He lives in Montreal. And in his lawsuit, he says Saudi officials in Canada met him in May, told him Crown Prince Mohammed bin Salman was unhappy with his activism. They asked him to come to the Saudi consulate for further discussion, and he declined. And he says that he and Jamal Khashoggi started working together on an initiative to organize a group of Twitter activists against the Saudi regime. And then this dissident got a text message with a link, supposedly a DHL package delivery, and he clicked on the link and later, a Canadian group, Citizen Lab, said it believed that he fell victim to a cellphone spyware from an Israeli-based company, NSO. He spoke with NPR's Shannon Van Sant, and he said he thinks the Saudis intercepted his Whatsapp text messages with Khashoggi, and that was a deciding factor that led to his death. Here's what he said.
OMAR ABDULAZIZ: For sure, the conversations between us played a major role in what happened to Jamal. And they found out what we were working on and what are these projects and why Jamal was behind them.
MARTIN: What do we know about this company that makes the spyware?
ESTRIN: NSO is its name. It's a very secretive company. It doesn't have a website. It was founded by three Israelis. Their first names form the initials NSO. And there are Israeli reports that the company recently sold its spyware technology to Saudi officials. The company defends itself. It says its products are only sold to governments and to law enforcement to fight terrorism and crime, but Israel is actually involved in this company in that Israeli government officials have to give the OK to let it sell its products abroad. This company has faced a lot of controversy. Mexican human rights activists and others say Mexican government officials hacked into their phones using this company's spyware - same accusations from a human rights activist in the United Arab Emirates. Amnesty International also says the software was used against one of its employees, and Amnesty is accusing Israel of allowing the spyware to be sold to regimes that violate human rights.
MARTIN: Well, considering the company's connections to the Israeli government, is the suit likely to go anywhere?
ESTRIN: It seems like it's more of a symbolic lawsuit, Rachel, to draw public attention to this issue. I think it's going to be hard to prove these claims in court, and the Israeli Defense Ministry has constantly defended its vetting of NSO technology sales abroad. And I should add that Israel is not the only place in the world where companies are developing spyware technology, but it is - Israel is a big player in the field.
MARTIN: And presumably, Saudi officials aren't weighing in on whether or not they actually bought this technology, confirming any connection.
ESTRIN: They're not, and it's very interesting. Saudi and Israeli ties are kind of under the radar, but this may be an example of some of those ties.
-
Comment by Riaz Haq on May 7, 2019 at 9:27pm
-
-
Comment by Riaz Haq on June 20, 2019 at 9:13am
-
#India says a #Pakistani spy used bots to lure 98 #Indian targets in Army, Navy and Air Force, including #BrahMos #Missile Project Engineer, on #Facebook using 'Whisper', 'Gravity Rat' malware.
http://toi.in/xozvDa41/a24gk via @timesofindia
A recent investigation revealed how a Pakistani spy on Facebook named Sejal Kapoor hacked into the computers of 98 Indian defence officials since 2015. She was also involved in the leak of classified files of BrahMos missile in 2018.
It has been revealed that the hacker targeted officials from Indian Army, Navy, Air Force, paramilitary forces and state police personnel in Rajasthan, Madhya Pradesh, Uttar Pradesh, and Punjab between 2015 and 2018, reported TOI.
The hacker deceived her targets by sharing pictures and videos using a software malware called "Whisper", which is reported to be connected to a third-party server in a West Asian country.
Sejal's involvement in last year's leakage of sensitive technical information to Pakistan was also established in the recent investigation.
In 2018, an engineer working at the BrahMos Aerospace Private Limited, Nishant Agarwal, was arrested for providing technical information on BrahMos missiles to Pakistan in a joint operation by the Uttar Pradesh and Maharashtra Anti-Terrorism Squad (ATS) as well as the Military Intelligence (MI).
It was then revealed that Agarwal exchanged sensitive information to Pakistan spy agency Inter-Services Intelligence (ISI) based on evidence found on his personal computer and Facebook chat records.
Apart from the "Whisper" application, another software that the spy used was "Gravity Rat." The Indian intelligence agencies say that both the software use "self-aware" detection techniques as well as VPN hiding mechanism that enables a hacker to use around 25 internet addresses. The complex malware technology is stated to not be easily identified by anti-malware software.
The five dozen chats recently uncovered by intelligence agency revealed that Sejal would "force install" the Whisper app on computers of the targeted officials, reported TOI.
"Instantly, after getting downloaded, the malware first prompts the user to key in a code. It's to ensure that the app is not a virus or malware. Immediately after that, it scans all latest attachments sent from the computer in emails or downloads. It then scans all files with photographs, databases of MS Word and MS Excel, by first verifying their encryption keys and then opening their passwords," said a senior intelligence officer, reported TOI.
According to Sejal's Facebook profile, the hacker is an employer of a company called "Growth Company" in Manchester, the UK. Experts have claimed that such cases of armed force officials "honey-trapped" into sharing classified information are a threat to India's national security.
Last year, a Border Security Force (BSF) soldier was arrested by Uttar Pradesh ATS on September 18 for sharing key information about the unit's operations to a female Pakistan ISI agent, who claimed to be a defence reporter.
-
Comment by Riaz Haq on December 19, 2019 at 1:38pm
-
#Israeli #spyware allegedly used to target #Pakistani officials' phones. The details are likely to fuel speculation that #India could have been using NSO #technology for domestic and international surveillance. #Modi #RAW #WhatsApp
https://www.theguardian.com/world/2019/dec/19/israeli-spyware-alleg...
The mobile phones of at least two dozen Pakistani government officials were allegedly targeted earlier this year with technology owned by the Israeli spyware company NSO Group, the Guardian has learned.
Scores of Pakistani senior defence and intelligence officials were among those who could have been compromised, according to sources familiar with the matter who spoke on the condition of anonymity.
The alleged targeting was discovered during an analysis of 1,400 people whose phones were the focus of hacking attempts in a two-week period earlier this year, according to the sources.
All the suspected intrusions exploited a vulnerability in WhatsApp software that potentially allowed the users of the malware to access messages and data on the targets’ phones.
The discovery of the breach in May prompted WhatsApp, which is owned by Facebook, to file a lawsuit against NSO in October in which it accused the company of “unauthorised access and abuse” of its services.
The lawsuit claimed intended targets included “attorneys, journalists, human rights activists, political dissidents, diplomats, and other senior foreign government officials”.
NSO has said it will vigorously contest the claim and has insisted that its technology is only used by law enforcement agencies around the world to snare criminals, terrorists and paedophiles.
The alleged targeting of Pakistani officials gives a first insight into how NSO’s signature “Pegasus” spyware could have been used for “state-on-state” espionage.
The details also raise fresh questions about how NSO’s clients use its spyware.
“This kind of spyware is marketed as designed for criminal investigations. But the open secret is that it also winds up being used for political surveillance and government-on-government spying,” said John Scott-Railton, a senior researcher at the Citizen Lab, an academic research group located at the University of Toronto that has worked with WhatsApp to help identify victims of the alleged hacks.
“Spyware companies are clearly contributing to the proliferation of state-on-state technological espionage. No government seems particularly immune. This is probably further stretching the patience of governments around the world with this industry,” he added.
The Pakistani embassies in London and Washington declined multiple requests for comment. WhatsApp declined to comment.
Representatives for NSO declined to comment on questions about whether the company’s software had been used for government espionage.
The company has previously said it considered it a “misuse” of its product if the software was used for anything other than the prevention of “serious crime and terrorism”.
While it is not clear who wanted to target Pakistani government officials, the details are likely to fuel speculation that India could have been using NSO technology for domestic and international surveillance.
The government of the Indian prime minister, Narendra Modi, is facing questions from human rights activists about whether it has bought NSO technology after it emerged that 121 WhatsApp users in India were allegedly targeted earlier this year.
The figure included about two dozen alleged victims who are journalists, activists and human rights lawyers, a fact that prompted Modi opponents in the Indian National Congress to seek a supreme court inquiry into the matter.
Pakistan has not publicised the alleged hack, but there are signs the government, led by the prime minister, Imran Khan, is taking steps to address the matter.
Dr Arslan Khalid, who serves as Khan’s top adviser on digital issues, has said in local press reports that the government is working on developing an alternative to WhatsApp
-
Comment by Riaz Haq on November 30, 2020 at 10:46am
-
Pakistan has established #Cyber Forensic Laboratory at NUST, and the #Computer Emergency Response Team (PAK-CERT). #Pakistan has made major progress in #Nuclear ‘Security and Control Measures’ category with an incredible (+25) points. https://moderndiplomacy.eu/2020/08/18/nti-2020-and-pakistans-cyber-...
Among countries with weapons-usable nuclear materials, Australia for the third time has been ranked at the first position in the sabotage ranking and for the fifth time for its security practices. Likewise, New Zealand and Sweden stand first in the ranking for countries without materials. It is very pertinent to highlight here that Pakistan’s commitment towards nuclear safety and security, has also been duly acknowledged. In this regard, since Pakistan has adopted new on-site physical protection and cyber security regulations, it has been appreciated in the index. This would likely further improve Pakistan’s existing insider threat prevention measures. Nevertheless, the 2020 NTI report has ranked Pakistan among the countries that have nuclear materials but its adherence to nuclear safety and security has been vindicated.
It is worth mentioning here that in the theft ranking for countries with nuclear materials, Pakistan has improved its ranking by an overall score of 7 points. In this regard, Pakistan has made major progress in the ‘Security and Control Measures’ category with an incredible (+25) points based on the new regulations. Also, Pakistan has improved in the Global Norms category with (+1) points. The strengthened laws and regulations have provided sustainable security benefits and resulted in improving Pakistan’s overall score. Moreover, Pakistan’s improvement in the Security and Control Measures category is quite significant. Over time, by improving +8 points in 2014, +2 points in 2016, and +6 points in 2018, Pakistan has steadily improved in the Security and Control Measures category. Owing to new regulations for on-site physical protection its score has improved since 2014. Whereas since 2018; the insider threat protection has also improved. When the report was first launched in 2012, since then Pakistan, unlike other states has improved its score in the security and control measure category with 25 points. This is an incredible improvement as it is the second-largest improvement among the related states.
At the national level, Pakistan has taken various initiatives including; the establishment of Cyber Forensic Laboratory at the National University of Science and Technology (NUST), and the Computer Emergency Response Team (PAK-CERT) to deal with cyber-related threats. Furthermore, the National Centre for Cyber Security at the Air University also aims at making cyberspace of Pakistan more secure. It has affiliated Research and Development Laboratories working on projects related to network security systems and smart devices. To maintain such a status, in the longer term, Pakistan needs to further expand the scope of its existing national cyber policy framework. This would enhance Pakistan’s capabilities to tackle cyber threats to nuclear security in a more efficient way.
Hence, the emergence of cyber threats to nuclear security both at the regional and the global levels needs to be addressed with greater cooperation among the states. Likewise, it is also essential to address the human factor for cyber security when insiders could unwittingly introduce or exacerbate cyber vulnerabilities. Pakistan needs to further enhance the role and increase the capacity of its specialized cyber workforce. In this regard, if required, the number of highly skilled technical staff may be increased keeping view of the emergent cyber threats to the nuclear facilities.
-
Comment by Riaz Haq on November 30, 2020 at 11:15am
-
Rank 2019
Rank 2020 Country Score 2019 Score 2020 % of Mobiles Infected with Malware Financial Malware Attacks (% of Users) % of Computers Infected with Malware % of Telnet Attacks by Originating Country (IoT) % of Attacks by Cryptominers Best Prepared for Cyberattacks Most Up-to-Date Legislation 1 1 Algeria 55.75 48.99 26.47 0.5 19.75 0.07 1.27 0.262 1 - 1 Tajikistan - 48.54 2.62 1.4 8.12 0.01 7.90 0.263 2 - 3 Turkmenistan - 48.39 4.89 1.1 5.84 0 7.79 0.115 2 - 4 Syria - 44.51 10.15 1.2 13.99 0.01 1.36 0.237 1 9 5 Iran 43.29 43.48 52.68 0.8 7.21 3.31 1.43 0.641 2 8 6 Belarus 45.09 41.64 2.10 2.9 13.34 0.05 2.35 0.578 3 6 7 Bangladesh 47.21 40.36 30.94 0.8 16.46 0.38 1.91 0.525 3.5 7 8 Pakistan 47.10 40.33 28.13 0.8 9.96 0.37 2.41 0.407 2.5 5 9 Uzbekistan 50.50 39.41 4.14 2.1 10.5 0.02 4.99 0.666 3 4 According to our study, Algeria is still the least cyber-secure country in the world despite its score improving slightly. With no new legislation (as was the same with all countries), it is still the country with the poorest legislation (only one piece of legislation — concerning privacy — is in place). It also scored poorly for computer malware infection rates (19.75%) and its preparation for cyberattacks (0.262). Nevertheless, only its score for lack of preparation that worsened over the last year (and its score for legislation which couldn’t get any worse). In all of the other categories, attacks declined, as was the common trend for most countries.
Other high-ranking countries were Tajikistan, Turkmenistan, Syria, and Iran, which took over from last year’s Indonesia, Vietnam, Tanzania, and Uzbekistan.
The highest-scoring countries per category were:
- Highest percentage of mobile malware infections – Iran – 52.68% of users
- Highest number of financial malware attacks – Belarus – 2.9% of users
- Highest percent of computer malware infections – Tunisia – 23.26% of users
- Highest percentage of telnet attacks (by originating country) – China – 13.78%
- Highest percentage of attacks by cryptominers – Tajikistan – 7.9% of users
- Least prepared for cyber attacks – Turkmenistan – 0.115
- Worst up-to-date legislation for cybersecurity – Algeria – 1 key category covered
Apart from Algeria, China was the only country that stayed at the top of one of these lists – all of the other countries are new since last year.
10 Tanzania 51.00 38.72 21.96 0.6 9.41 0.03 4.35 0.642 1.5
Comment
You need to be a member of PakAlumni Worldwide: The Global Social Network to add comments!
Twitter Feed
Live Traffic Feed
Sponsored Links
South Asia Investor Review
Investor Information Blog
Haq's Musings
Riaz Haq's Current Affairs Blog
Please Bookmark This Page!
Blog Posts
Pakistani Student Enrollment in US Universities Hits All Time High
Pakistani student enrollment in America's institutions of higher learning rose 16% last year, outpacing the record 12% growth in the number of international students hosted by the country. This puts Pakistan among eight sources in the top 20 countries with the largest increases in US enrollment. India saw the biggest increase at 35%, followed by Ghana 32%, Bangladesh and…
ContinuePosted by Riaz Haq on April 1, 2024 at 5:00pm
Agriculture, Caste, Religion and Happiness in South Asia
Pakistan's agriculture sector GDP grew at a rate of 5.2% in the October-December 2023 quarter, according to the government figures. This is a rare bright spot in the overall national economy that showed just 1% growth during the quarter. Strong performance of the farm sector gives the much needed boost for about …
ContinuePosted by Riaz Haq on March 29, 2024 at 8:00pm
© 2024 Created by Riaz Haq.
Powered by
![]()
https://nyti.ms/2H0Oekx
Chinese intelligence agents acquired National Security Agency hacking tools and repurposed them in 2016 to attack American allies and private companies in Europe and Asia, a leading cybersecurity firm has discovered. The episode is the latest evidence that the United States has lost control of key parts of its cybersecurity arsenal.
Based on the timing of the attacks and clues in the computer code, researchers with the firm Symantec believe the Chinese did not steal the code but captured it from an N.S.A. attack on their own computers — like a gunslinger who grabs an enemy’s rifle and starts blasting away.
The Chinese action shows how proliferating cyberconflict is creating a digital wild West with few rules or certainties, and how difficult it is for the United States to keep track of the malware it uses to break into foreign networks and attack adversaries’ infrastructure.
The losses have touched off a debate within the intelligence community over whether the United States should continue to develop some of the world’s most high-tech, stealthy cyberweapons if it is unable to keep them under lock and key.
The Chinese hacking group that co-opted the N.S.A.’s tools is considered by the agency’s analysts to be among the most dangerous Chinese contractors it tracks, according to a classified agency memo reviewed by The New York Times. The group is responsible for numerous attacks on some of the most sensitive defense targets inside the United States, including space, satellite and nuclear propulsion technology makers.
Now, Symantec’s discovery, unveiled on Monday, suggests that the same Chinese hackers the agency has trailed for more than a decade have turned the tables on the agency.
Some of the same N.S.A. hacking tools acquired by the Chinese were later dumped on the internet by a still-unidentified group that calls itself the Shadow Brokers and used by Russia and North Korea in devastating global attacks, although there appears to be no connection between China’s acquisition of the American cyberweapons and the Shadow Brokers’ later revelations.
But Symantec’s discovery provides the first evidence that Chinese state-sponsored hackers acquired some of the tools months before the Shadow Brokers first appeared on the internet in August 2016.
Repeatedly over the past decade, American intelligence agencies have had their hacking tools and details about highly classified cybersecurity programs resurface in the hands of other nations or criminal groups.
--------------------
The N.S.A. used sophisticated malware to destroy Iran’s nuclear centrifuges — and then saw the same code proliferate around the world, doing damage to random targets, including American business giants like Chevron. Details of secret American cybersecurity programs were disclosed to journalists by Edward J. Snowden, a former N.S.A. contractor now living in exile in Moscow. A collection of C.I.A. cyberweapons, allegedly leaked by an insider, was posted on WikiLeaks.