PakAlumni Worldwide: The Global Social Network
The Global Social Network
Proliferation of Cyber Hacking Tools in Pakistan
Many intelligence agencies are turning to the use of smartphone malware and spyware for the purpose of hacking and surveillance. The list of such agencies includes but not limited to US CIA, NSA, Mossad, RAW, MI6, ISI and others. Global proliferation of cyber hacking tools appears to have been accelerated with the US CIA's loss of control of its hacking tools including spyware, malware, viruses and trojans.
Stealth Mango and Tangelo:
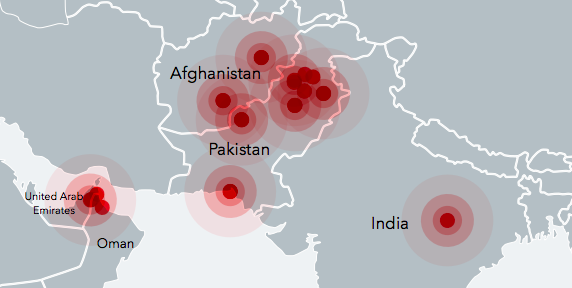
Lookout, an American mobile security firm based in San Francisco, has recently published a report claiming that a "group or individuals that are believed to belong to the Pakistani military "has developed and released a "set of custom Android and iOS surveillanceware tools we’re respectively calling Stealth Mango and Tangelo". The report says: "These tools have been part of a highly targeted intelligence gathering campaign we believe is operated by members of the Pakistani military". The countries affected by it include Afghanistan, India, Iraq, Pakistan and the United Arab Emirates, according to Lookout report.
The targets in Pakistan include members of the foreign diplomatic corps who have visited conflict zones, particularly parts of Balochistan, and Pakistani officials involved in internal corruption investigations.
The goal of the Lookout report is to sell their security software as obvious from their concluding summary below:
"Stealth Mango and Tangelo is yet another example among the numerous campaigns we have uncovered (Dark Caracal, ViperRAT, FrozenCell, etc.) where threat actors are developing in-house custom surveillanceware. The actor behind Stealth Mango has stolen a significant amount of sensitive data from compromised devices without the need to resort to exploits of any kind. The actors that are developing this surveillanceware are also setting up their own command and control infrastructure and in some cases encountering some operational security missteps, enabling researchers to discover who the targets are and details about the actors operating it that otherwise are not as easily obtained. Relevant data has already been shared with the appropriate authorities. Lookout customers are protected against Stealth Mango and Tangelo and have been for several months since the beginning of the investigation."
Amnesty International Allegations:
Amnesty International has alleged that attackers are using fake online identities and social media profiles to "ensnare Pakistani human rights defenders online and mark them out for surveillance and cybercrime". The report titled "Human Rights Under Surveillance: Digital Threats against Human Righ..." claims that Diep Saeeda, a Lahore-based human rights activist, has been targeted by a "network of individuals and companies based in Pakistan that are behind the creation of some of the tools seen in surveillance operations used to target individuals in Pakistan".
Amnesty says that "over the course of several months, Amnesty International used digital forensic techniques and malware analysis to identify the infrastructure and web pages connected to online attacks on human rights activists in Pakistan". "Amnesty International’s Technology and Human Rights team has been able to trace these attacks to a group of individuals based in Pakistan".
Proliferation of Hacking Tools:
In 2017, Wikileaks revealed that the American intelligence agency CIA has "lost control of the majority of its hacking arsenal including malware, viruses, trojans, weaponized "zero day" exploits, malware remote control systems and associated documentation." The Wikileaks noted that that "the CIA made these systems unclassified".
Wikileaks said: "In what is surely one of the most astounding intelligence own goals in living memory, the CIA structured its classification regime such that for the most market valuable part of "Vault 7" — the CIA's weaponized malware (implants + zero days), Listening Posts (LP), and Command and Control (C2) systems — the agency has little legal recourse".
FBI agents have since arrested 29-year-old former CIA software engineer Joshua A. Schulte as a prime suspect in the release of the CIA documents via Wikileaks, according to New York Times.
It appears that the CIA's "hacking arsenal" is now being modified and used by many state and non-state actors to carry out hacking and surveillance of their targets around the world. The proliferation of cyber hacking tools appears to be a lot easier than the proliferation of the nuclear weapons technology.
Summary:
A report by American mobile security software vendor Lookout claims that individuals and groups connected to the Pakistani military are using spyware and malware tools on targets in Afghanistan, Pakistan, India and UAE. Amnesty International alleges that Pakistan intelligence agencies are "network of individuals and companies based in Pakistan that are behind the creation of some of the tools seen in surveillance operations used to target individuals in Pakistan".
Many intelligence agencies are turning to the use of smartphone malware and spyware for the purpose of hacking and surveillance. The list of such agencies includes but not limited to US CIA, NSA, Mossad, RAW, MI6, ISI and others. Global proliferation of cyber hacking tools appears to have been accelerated when the US CIA lost control of its hacking tools including malware, viruses and trojans.
Related Links:
Pakistan Operation Arachnophobia
Revolution in Military Affairs: Cyberweapons and Robots
Pakistani-American Founder of Fireeye Cyber Firm
Pakistan Boosts Surveillance to Fight Terror
Pakistan's Biometric Registration Database
Ex Indian Spy Documents RAW's Successes in Pakistan
Intelligence Failures in Preventing Daily Carnage in Pakistan
What If Musharraf Had Said NO to US After 911?
Pakistani Computer Scientist Fights Terror
-
Comment by Riaz Haq on November 30, 2020 at 11:24am
-
Pakistan’s cyberspace at the mercy of hackers
Officials, experts say need to enact cybersecurity, data protection laws dire
https://tribune.com.pk/story/1938526/8-pakistans-cyberspace-mercy-h...
As things stand, Pakistan counts itself among countries considered unsafe for internet users. The 2017 Global Cybersecurity Index places Pakistan at 67 on a list of 165 countries ranked according to how safe their cyber-environments are. Of Pakistan’s roughly 45 million internet users, a staggering 25% have been attacked one way or another by hackers.
In particular, the cyberattacks on Pakistani banks reported late last year underscored the woeful inadequacy of current cybercrime laws. In that episode, hackers stole credit card details of more than 20,000 customers from 22 Pakistani banks and leaked them over the ‘dark web’ – portions of the internet not open to public view and accessible only through special software.
Federal Investigation Agency (FIA) officials complain that current cybercrime laws do not recognise invasion of online privacy and unauthorised access to personal data as criminal offenses, putting Pakistani internet users at great risk of misuse of private information. To further complicate matters, social media networks and email services are not bound to relinquish any information for investigation.
Both officials and experts agree there is a pressing need to formulate an enforceable national cybersecurity framework and set up computer emergency response teams (CERTs) to prosecute and prevent such incidents.
Speaking to The Express Tribune, FIA Additional Director General Ammar Jaffery compared the lack of a legal framework covering cybersecurity to leaving a house unlocked.
“Would you not be practically inviting thieves to rob you? This is exactly what Pakistan’s current situation is with regards to cybersecurity,” he said, stressing the need to immediately introduce laws pertaining to cybersecurity. “Better cybersecurity supported by robust laws would deter would-be criminals from engaging in cybercrimes.”
“The Prevention of Electronic Crimes Act (PECA) which we have right now has some loopholes,” said Zeeshan Riaz, a lawyer who specialises in cybercrime cases. “Take data theft for example, there is no proper law covering it. If someone’s data was stolen today, authorities would encounter difficulties in determining cognisable and non-cognisable offenses, and obtaining warrants.”
-
Comment by Riaz Haq on February 11, 2021 at 1:32pm
-
Indian cyber-spy ‘Confucius’ targets #Pakistan, #Kashmir: #Indian hackers using #malware to target Pakistani military officials, Pak's top #nuclear regulator and #Indian election officials in #Indian Occupied Kashmir, says San Francisco-based Lookout Inc.
https://www.smh.com.au/world/asia/indian-cyber-spy-confucius-target...
Oakland, California: A hacking group with ties to the Indian military adopted a pair of mobile surveillance tools to spy on geopolitical targets in Pakistan and Kashmir amid persistent regional tensions between the nuclear-armed neighbours, according to a report from a cyber security company.
The group is known for commandeering legitimate web services in South Asia and embedding surveillance tools or malware inside apps and services to conduct espionage. Since 2017, and as recently as December, the hackers have relied on spyware to target Pakistani military officials, the country’s top nuclear regulator and Indian election officials in the disputed state of Kashmir, according to the report released by San Francisco-based Lookout Inc on Thursday.
The campaign appears to be just the latest example of hackers targeting sensitive security targets with social engineering tactics - luring victims to download malicious files disguised as benign applications. What’s unique about attacks by the group, dubbed Confucius, is the extent to which its operators go to veil their efforts, experts say.
Using knock-off web applications disguised as Google security tools and popular regional chat and dating applications, Confucius managed to access 156 victims’ devices in a trove of data recently discovered by the research team. The files and related logs were found in unsecured servers used by the attack group, according to the report. Most of the users who recently accessed those servers were based in Northern India.
Once the attackers penetrate a device, they scrape it for data, including call logs, contacts, geolocation, images and voice notes. In some cases, the hackers took screen shots of the devices and recorded phone calls. In at least one instance, intruders got inside the device of a Pakistani Air Force service member and viewed a contact list filled with other Air Force officials, said Apurva Kumar, Lookout’s staff security intelligence engineer.
“While their technical tools and malwares might not be that advanced, the Confucius threat actor invests human time to gain trust from their targets,” said Daniel Lunghi, threat researcher at the cyber security firm, Trend Micro. “And in certain sensitive fields where people are more cautious, it might be what makes the difference.”
In two cases, researchers discovered that hackers stole the contents of WhatsApp chat conversations from 2017 and 2018 between officials at the Pakistan Nuclear Regulatory Authority, Pakistan Atomic Energy Commission and unknown third-parties. Then in April 2019, in the midst of India’s latest national election, the attackers burrowed into the device of an election official in the Pulwama region of Kashmir, where months earlier an Indian security convoy was attacked by a Pakistan-based Islamic terrorist in a deadly explosion.
Kumar said she couldn’t disclose the details of the stolen data.
Her research indicates the espionage campaign ramped up in 2018 after unknown hackers breached the commercial surveillance-ware provider, Retina-X Studios. Hornbill, one of the malware tools used by the attackers, shares code similarities with Retina-X’s Mobile Spy products. Another piece of malicious software called Sunbird, which is capable of remotely commandeering a user’s device, appears to be rooted in code for a stalkerware service called, BuzzOutLoud, based in India.
-
Comment by Riaz Haq on May 14, 2021 at 7:58pm
-
Suspected Pakistani spies use catfishing, stealthy hacking tools to target Indian defense sector
https://www.cyberscoop.com/pakistan-india-hacking-cyber-catfishing/
For years, suspected Pakistani hackers have sought to pry their way into Indian government computer networks as part of broader dueling cyber-espionage campaigns between the rival nations.
Over the last 18 months, a spying group known as Transparent Tribe has expanded its use of a hacking tool capable of stealing data and taking screenshots from computers, according to research published Thursday by Talos, Cisco’s threat intelligence unit. Hackers also are going after additional targets beyond Indian military personnel, including defense contractors and attendees of Indian government-sponsored conferences.
Talos did not mention Pakistan in its research, but multiple security researchers told CyberScoop the Transparent Tribe group is suspected of operating on behalf of the Pakistani government. Similarly, research from email security firm Proofpoint has previously linked a Pakistan-based company to the development of the group’s malicious code.
Talos’ findings reflect a relentless appetite for defense-related secrets among hacking groups with suspected links to Pakistan and India, two nuclear-armed neighbors prone to territorial disputes.
Transparent Tribe’s improved capabilities are also a case study in how governments not known for their hacking prowess can evolve. While U.S. officials regularly name China, Russia, Iran and North Korea as the most capable of cyber actors, governments the world over appear to be buying off-the-shelf hacking kits or developing their own tools.
A 2019 study backed by the Department of Homeland Security and the Office of the Director of National Intelligence found that countries such as Vietnam and the United Arab Emirates had made sharp advances in their hacking capabilities in recent years.
“A proliferation and commodification of cyber offensive capabilities is reshaping the cyber balance of power, enabling an expanded array of actors to use cyber for geopolitical impact or economic gain,” said the study, whose authors included government and private-sector executives.
Asheer Malhotra, a Talos threat researcher, said that Transparent Tribe “has become more and more aggressive in terms of targeting, expanding operations and evolving their tactics.”
For example, the group has recently used breached websites to deliver its malicious code to victims, rather than simply embedding the code in an email, according to Talos. That makes the intrusion attempts harder to detect. As of this week, the hackers were using a website that mimics an Indian government benefits portal to try to infect government employees, Malhotra said.
Transparent Tribe has also made a habit of appealing to their targets’ romantic desires. The hackers in 2019 and 2020 sent malware-laced photos of alluring women to targets, according to Talos. India’s defense minister warned about Pakistan’s alleged use of that broader tactic in 2019, and said that young military recruits were trained to spot the subterfuge.
Hackers with suspected ties to India have also repeatedly gone after Pakistani targets. In February, mobile security firm Lookout uncovered a years-long hacking campaign that aligned with Indian interests and sought to bug the phones of people in Pakistan and elsewhere. Among the suspected targets was a job candidate at the Pakistan Atomic Energy Commission.
“This is business as usual from an espionage perspective,” Malhotra said when asked if there was any fluctuation in digital spying that coincided with a spike in tensions between India and Pakistan. “There have always been military and political tensions between the two states since their inception.”
-
Comment by Riaz Haq on May 14, 2021 at 8:05pm
-
The ransomware pandemic
Why it matters: Crippling a major U.S. oil pipeline this weekend initially looked like an act of war — but it's now looking like an increasingly normal crime, bought off-the-shelf from a "ransomware as a service" provider known as DarkSide.
"We are on the cusp of a global pandemic," said Christopher Krebs, the first director of the Cybersecurity and Infrastructure Security Agency, told Congress last week. The virus causing the pandemic isn't biological, however. It's software.
Why it matters: Crippling a major U.S. oil pipeline this weekend initially looked like an act of war — but it's now looking like an increasingly normal crime, bought off-the-shelf from a "ransomware as a service" provider known as DarkSide.
Driving the news: Colonial runs the largest refined products pipeline in the country, transporting over 100 million gallons per day. It was shut down on Friday in response to a ransomware attack, and will be reopened in "an incremental process" over the course of this week, per a corporate statement.
- That's faster than the market expected — energy prices fell after the statement was released, after rising on the initial shutdown news.
The big picture: No company is safe from ransomware, and often the lines between criminals and state actors can be fuzzy. Preventing even bigger future attacks will require a so-far elusive degree of coordination between the public and private sectors in dozens — if not hundreds of countries.
- Threat level: Very high. "Cybersecurity will be the issue of this decade in terms of how much worse it is going to get," IBM CEO Arvind Krishna told reporters Monday.
- Currently, per Forrester analyst Allie Mellen, companies' main strategy is to pay up if hit — and to try to be slightly less vulnerable to attack than their competitors. "What do security pros do right now to lower their risk in the face of future ransomware attacks? Outrun the guy next to you,” Mellen says.
Between the lines: If anything, Colonial Pipeline was lucky that it is so important to the functioning of the American economy. Its systemic status helped to mobilize the full resources of the U.S. government, and even elicited an apology, of sorts, from DarkSide.
- “Our goal is to make money and not creating problems for society," said the group in a statement on the dark web. "From today, we introduce moderation and check each company that our partners want to encrypt to avoid social consequences.”
What they're saying: "There is no silver bullet for solving this challenge," concludes a major report on combating ransomware from the Institute for Security + Technology. "No single entity alone has the requisite resources, skills, capabilities, or authorities to significantly constrain this global criminal enterprise."
- The fight will require the active involvement of the National Security Council, says the report, as well as much more regulation of cryptocurrency, which is invariably used to pay the ransom.
- It will also require a major upgrade of technology systems at the state and local level, very few of which have been migrated to cloud-based systems that can try to keep one step ahead of the bad guys.
The bottom line: The Colonial Pipeline attack was so big that it couldn't help but make headlines. But most attacks are quietly paid off with no fanfare and no publicity, making it extremely difficult to gauge the true scale of the problem.
-
Comment by Riaz Haq on June 28, 2021 at 7:04am
-
IISS Report: #India has some #cyber-intelligence & offensive cyber capabilities but they are focused on #Pakistan. #Delhi is building new capability with the help of key international partners – including #US, #UK & #France. #Cyberwar https://indianexpress.com/article/india/focused-on-pakistan-rather-... via @IndianExpr
Cyberpower, in the study, is measured on seven parameters: from strategy to cybersecurity. India’s reform in cyber governance has been slow. It should better harness its digital start-up ecosystem, says the study.
Greg Austin, who leads the IISS programme on Cyber, Space and Future Conflict and played a leading role in the preparation of the report, told The Indian Express Sunday: “India has some cyber-intelligence and offensive cyber capabilities but they are regionally focused, principally on Pakistan. It is currently aiming to compensate for its weaknesses by building new capability with the help of key international partners – including the US, the UK and France – and by looking to concerted international action to develop norms of restraint.”
The report said that India’s approach towards institutional reform of cyber governance has been “slow and incremental”, with key coordinating authorities for cyber security in the civil and military domains established only as late as 2018 and 2019 respectively.
These work closely with the main cyber-intelligence agency, the National Technical Research Organisation.
“India has a good regional cyber-intelligence reach but relies on partners, including the United States, for wider insight”, the report said.
It said that the strengths of the Indian digital economy include a vibrant start-up culture and a very large talent pool. “The private sector has moved more quickly than the government in promoting national cyber security.”
The country is active and visible in cyber diplomacy but has not been among the leaders on global norms, preferring instead to make productive practical arrangements with key states, the report said.
“India is a third-tier cyber power whose best chance of progressing to the second tier is by harnessing its great digital-industrial potential and adopting a whole-of-society approach to improving its cyber security,” the report said.
The report also assessed China’s cyber power as clearly inferior to that of the US, and substantially below the combined cyber power of the US network of alliances.
The countries covered in this report are US, United Kingdom, Canada and Australia (four of the Five Eyes intelligence allies); France and Israel (the two most cyber-capable partners of the Five Eyes states); Japan (also an ally of the Five Eyes states, but less capable in the security dimensions of cyberspace, despite its formidable economic power); China, Russia, Iran and North Korea (the principal states posing a cyber threat to Western interests); and India, Indonesia, Malaysia and Vietnam (four countries at earlier stages in their cyber-power development). It is an ongoing study, which will cover a total of 40 countries, including Germany, Singapore, Nigeria among others.
India has been put in the third tier meant for countries that have strengths or potential strengths in some of these categories but “significant weaknesses” in others. Also in this category are: Japan, Iran, Indonesia, Vietnam, Malaysia and North Korea.
In the second tier, with world-leading strengths in “some” categories are: Australia, Canada, China, France, Israel, Russia and the United Kingdom.
-
Comment by Riaz Haq on June 28, 2021 at 9:32am
-
IISS: Cyber Capabilities and National Power: A Net Assessment
London-based THE INTERNATIONAL INSTITUTE FOR STRATEGIC STUDIES
https://www.iiss.org/blogs/research-paper/2021/06/cyber-capabilitie...
India has frequently been the victim of cyber attacks, including on its critical infrastructure, and has attributed a significant proportion of them to China or Pakistan. CERT-In reported, for example, that there were more than 394,499 incidents in 2019,44 and 2020 saw an upsurge in attacks from China.45 Of particular concern to the Indian government are cyber attacks by North Korea that use Chinese digital infrastructure.46 The vast major- ity of the cyber incidents flagged by CERT-In appear to have been attempts at espionage,47 but they could also have resulted in serious damage to the integrity of
Indian networks and platforms. In 2020, India had the second-highest incidence of ransomware attacks in the world48 and the government banned 117 Chinese mobile applications because of security concerns.49
---------
Public statements by Indian officials and other open- source material indicate that India has developed rela- tively advanced offensive cyber capabilities focused on Pakistan. It is now in the process of expanding these capabilities for wider effect.
India reportedly considered a cyber response against Pakistan in the aftermath of the November 2008 terror- ist attacks in Mumbai, with the NTRO apparently at the forefront of deliberations.67 A former national security advisor has since indicated publicly that India pos- sesses considerable capacity to conduct cyber-sabotage operations against Pakistan,68 which appears credible
--------------------
Overall, India’s focus on Pakistan will have given it useful operational experience and some viable regional offensive cyber capabilities. It will need to expand its cyber-intelligence reach to be able to deliver sophisti- cated offensive effect further afield, but its close collab- oration with international partners, especially the US, will help it in that regard.
----------------
Raj Chengappa and Sandeep Unnithan, ‘How to Punish Pakistan’, India Today, 22 September 2016, https://www. indiatoday.in/magazine/cover-story/story/20161003-uri- attack-narendra-modi-pakistan-terror-kashmir-nawaz-sharif- india-vajpayee-829603-2016-09-22.
-
Comment by Riaz Haq on June 29, 2021 at 7:54am
-
Pakistan-linked hackers targeted Indian power company with ReverseRat
https://thehackernews.com/2021/06/pakistan-linked-hackers-targeted-...
A threat actor with suspected ties to Pakistan has been striking government and energy organizations in the South and Central Asia regions to deploy a remote access trojan on compromised Windows systems, according to new research.
"Most of the organizations that exhibited signs of compromise were in India, and a small number were in Afghanistan," Lumen's Black Lotus Labs said in a Tuesday analysis. "The potentially compromised victims aligned with the government and power utility verticals."
Some of the victims include a foreign government organization, a power transmission organization, and a power generation and transmission organization. The covert operation is said to have begun at least in January 2021.
The intrusions are notable for a number of reasons, not least because in addition to its highly-targeted nature, the tactics, techniques, and procedures (TTPs) adopted by the adversary rely on repurposed open-source code and the use of compromised domains in the same country as the targeted entity to host their malicious files.
At the same time, the group has been careful to hide their activity by modifying the registry keys, granting them the ability to surreptitiously maintain persistence on the target device without attracting attention.
Explaining the multi-step infection chain, Lumen noted the campaign "resulted in the victim downloading two agents; one resided in-memory, while the second was side-loaded, granting threat actor persistence on the infected workstations."
The attack commences with a malicious link sent via phishing emails or messages that, when clicked, downloads a ZIP archive file containing a Microsoft shortcut file (.lnk) and a decoy PDF file from a compromised domain.
The shortcut file, besides displaying the benign document to the unsuspecting recipient, also takes care of stealthily fetching and running an HTA (HTML application) file from the same compromised website.
The lure documents largely describe events catering to India, disguising as a user manual for registering and booking an appointment for COVID-19 vaccine through the CoWIN online portal, while a few others masquerade as the Bombay Sappers, a regiment of the Corps of Engineers of the Indian Army.
-
Comment by Riaz Haq on November 16, 2021 at 7:54am
-
Facebook says hackers in Pakistan targeted Afghan users amid government collapse
https://www.reuters.com/world/asia-pacific/exclusive-facebook-says-...
Hackers from Pakistan used Facebook to target people in Afghanistan with connections to the previous government during the Taliban's takeover of the country, the company's threat investigators said in an interview with Reuters.
Facebook (FB.O) said the group, known in the security industry as SideCopy, shared links to websites hosting malware which could surveil people's devices. Targets included people connected to the government, military and law enforcement in Kabul, it said. Facebook said it removed SideCopy from its platform in August.
The social media company, which recently changed its name to Meta, said the group created fictitious personas of young women as "romantic lures" to build trust and trick targets into clicking phishing links or downloading malicious chat apps. It also compromised legitimate websites to manipulate people into giving up their Facebook credentials.
"It's always difficult for us to speculate as to the end goal of the threat actor," said Facebook's head of cyber espionage investigations, Mike Dvilyanski. "We don't know exactly who was compromised or what the end result of that was."
Major online platforms and email providers including Facebook, Twitter Inc (TWTR.N), Alphabet Inc's (GOOGL.O) Google and Microsoft Corp's (MSFT.O) LinkedIn have said they took steps to lock down Afghan users' accounts during the Taliban's swift takeover of the country this past summer. read more
Facebook said it had not previously disclosed the hacking campaign, which it said ramped up between April and August, due to safety concerns about its employees in the country and the need for more work to investigate the network. It said it shared information with the U.S. State Department at the time it took down the operation, which it said had appeared "well-resourced and persistent."
-
Comment by Riaz Haq on January 29, 2022 at 10:40am
-
Mr. Modi has used the Israeli spyware to not only spy on his critics at home but also his perceived enemies abroad. Pakistani Prime Minister Imran Khan is among the most prominent targets of the Modi government's cyber attacks, according to a recently released Project Pegasus report. The Indian government has neither confirmed nor denied the report. The focus of the report is the use of the Israeli-made spyware by about a dozen governments to target politicians, journalists and activists. The users of the Pegasus software include governments of Bahrain, Morocco, Saudi Arabia, India, Mexico, Hungary, Azerbaijan, Togo and Rwanda.
http://www.riazhaq.com/2022/01/ny-times-modi-bought-israeli-pegasus...
-
Comment by Riaz Haq on July 7, 2022 at 7:51am
-
National Center for Cyber Security For Cyber Threats
Becoming an anonymous personality is a super easy task in the online space. All that one needs to do is hide the IP. The IP address makes it easier to trace online activities. You can find your IP address on What Is My IP. However, just because cyber threats exist, it does not mean one can prevent oneself from engaging in online activities. With proper digital hygiene along with government efforts, a country can mitigate cyber threats.
https://nation.com.pk/2022/07/07/the-role-of-national-center-for-cy...
In 2018, the Government of Pakistan established the National Centre for Cyber Security or NCCS. It was a joint initiative of the Planning Commission and Higher Education Commission. The body currently works in cybercrime forensics, smart devices, and network security.
New ways of committing cyber crimes are emerging with each passing year. Therefore, research and development are critical in fighting different cyber crimes. It is where the role of the National Center for Cyber Security comes in. NCCS deals with both applied and theoretical areas for fighting cybercrime.
It is known for its research on areas like Cyber Reconnaissance, Cybercrime Investigations, Blockchain Security, Digital Forensics, IoT Security, Intrusion Detection Systems, Mobile Phone Security, Internet Security and Privacy, Critical Infrastructure Security and Malware Analysis.
Cyber Security Policy Of Pakistan Is Evolving
In addition to bodies like NCCS, it is also important to have a solid cybersecurity policy. The Government of Pakistan recently approved a new cybersecurity policy to fight electronic crime. The policy will prove to be helpful for both the public and private institutions in fighting cybercrime. The policy will birth a secure cyber ecosystem in the country with the help of new governance and institutional framework. It will additionally support a computer emergency response team and a security operations centre at the institutional, sector and national level.
Further, the Government of Pakistan will work on improving general awareness of cyber security amongst the passes through public awareness campaigns, skill development and training programs.
Why Is Cyber Security Knowledge Important?
Security awareness is important in all sectors, including the domain of cyber security too. The interconnected system is essential to survive in the current digitised world. However, it comes with a risk a cyber security knowledge can mitigate. Without proper cyber security knowledge, it is easy to fall prey to online crime. The result will be that people will start losing their trust in the digital world, which can prove dangerous for any country in the digital age of digitisation.
Further, it is not enough to ensure the technology and infrastructure required to support it. Government should inform the people about the risks and help them fight it. Only through these methods can a country lay a strong foundation for further digitisation of the country.
Pakistan’s ranking on the Global CyberSecurity Index is disappointing. Therefore, the newly brought cyber security policy was a much-needed change to improve its ranking in future studies. With strong cyber security laws, Pakistan can promote easy socio-economic development. Thankfully, the Government of Pakistan is working towards it. For instance, a cyberattack on any Pakistan institution under the new policy will be considered an act of aggression against national sovereignty. The government will take all the necessary steps to punish the offender for dealing with it.
Comment
- ‹ Previous
- 1
- 2
- 3
- Next ›
Twitter Feed
Live Traffic Feed
Sponsored Links
South Asia Investor Review
Investor Information Blog
Haq's Musings
Riaz Haq's Current Affairs Blog
Please Bookmark This Page!
Blog Posts
Pakistani Student Enrollment in US Universities Hits All Time High
Pakistani student enrollment in America's institutions of higher learning rose 16% last year, outpacing the record 12% growth in the number of international students hosted by the country. This puts Pakistan among eight sources in the top 20 countries with the largest increases in US enrollment. India saw the biggest increase at 35%, followed by Ghana 32%, Bangladesh and…
ContinuePosted by Riaz Haq on April 1, 2024 at 5:00pm
Agriculture, Caste, Religion and Happiness in South Asia
Pakistan's agriculture sector GDP grew at a rate of 5.2% in the October-December 2023 quarter, according to the government figures. This is a rare bright spot in the overall national economy that showed just 1% growth during the quarter. Strong performance of the farm sector gives the much needed boost for about …
ContinuePosted by Riaz Haq on March 29, 2024 at 8:00pm
© 2024 Created by Riaz Haq.
Powered by
![]()
You need to be a member of PakAlumni Worldwide: The Global Social Network to add comments!
Join PakAlumni Worldwide: The Global Social Network